16 Expert Cybersecurity Tips for Small Businesses
1
Videos
10 Min.
Read Time
Cybersecurity
Topic
4
Free Downloads
Share This Page:
Table of Contents
Overview
Our experts have shared their top cybersecurity tips for small businesses. Why? To give you a solid, proven strategy to secure your organization.
Every day, we hear a new news story about a large organization becoming a victim of cybercrime – such as the Microsoft data breach in March 2022.
Despite what the news depicts, small- to medium-sized businesses (SMBs) are just as much at risk. But many leaders don’t know how to protect themselves efficiently.
With this defense-in-depth strategy, you can rest assured you’re effectively mitigating the risks your organization faces.
In a hurry? Download the strategy guide below.
Discover 16 essential cybersecurity controls your small business needs to reduce risk and avoid costly damages associated with a cyberattack.
But where do you begin? What elements should your IT team focus their energy on? Where do you allocate funds first?
As an experienced managed IT provider that protects small businesses daily, we have created this guide to answer your questions – providing you with the strategies you need to become a more secure organization.
Let’s get started!
How You Can Reduce Your Risk
You may have to work within tight budget constraints when it comes to addressing your organization’s security challenges. But when you implement this strategic approach, it is possible to create an effective security plan.
A useful analogy is to think of your SMB as a kingdom. “The kingdom represents defense in depth,” said Reid Johnston, Teal CIO & Cofounder. “It illustrates that your business is a kingdom, and there are many layers you need to protect it – both inside and around it.”

How to Use This Guide
Below, you will find two separate sections to help you prioritize the key security elements.
Part One: Cybersecurity Tips for Small Businesses
In this section, we have identified ten cybersecurity tips for small businesses. Your SMB needs these foundational cybersecurity elements as soon as possible to mitigate risk. We have ranked them in order of priority.
For instance, if you already have inventory management covered, but have not established policies and processes, we recommend you start there.
Part Two: 6 Additional Small Business Cybersecurity Defense Tips
This section includes an additional six elements your business should incorporate into your plan once the first ten priorities are complete.
10 Cybersecurity Tips for Small Businesses
SMBs are often sought out by cybercriminals because they know you’re not investing enough time and money into cybersecurity – if at all. Begin implementing these 10 cybersecurity elements to safeguard your organization’s future.
1. Take Inventory
The first cybersecurity tip for small businesses is inventory. Now, inventory isn’t just about physical devices. It’s also about software installed on your endpoints, your hardware, and your people. You must know exactly what you’re protecting – otherwise you can’t protect it.
Additionally, if you have personally identifiable information (PII), personal health information (PHI), trade secrets, or company secrets you’ll want to take inventory of this type of information as well.
2. Establish Information Security Policies & Processes
This is your kingdom’s decree. It provides a framework for protecting sensitive information and IT assets. Robust security policies help you efficiently allocate resources, ensure compliance with regulations, and safeguard against cyber threats.
Simply put, you will establish policies for how employees should handle and protect your information assets, computer, and network systems. It should also clearly outline the consequences of violating your business’s cybersecurity policies.
If you are starting from scratch, we recommend SANS. They have a good set of free policy templates you can download, tweak, and implement. Many of our clients start this way but make sure you modify it to fit your organization.
3. Implement Security Awareness Training
Security awareness training is your kingdom’s library. Your valued employees are typically the weakest link in your security stack, and they require education. Verizon (2021) reported that 85% of data breaches involve the human element. This is commonly achieved through social engineering attacks, like:
- Tailgating
- Pretexting
- Whaling
- Baiting
- Quid Pro Quo
- Phishing
- Vishing
- Smishing
- Scareware
Set your users up for success by training them – frequently. Security training is something that should be repetitive. Use these tips to create effective cybersecurity awareness training.
Discover 16 essential cybersecurity controls your small business needs to reduce risk and avoid costly damages associated with a cyberattack.
4. Have Antivirus & Endpoint Security
Deploy a best-in-class antivirus and anti-malware solution on your company’s endpoints. Endpoint protection is your calvary. They help your business keep critical systems, intellectual property, customer data, employees, and guests safe from:
- Ransomware
- Malware
- And other cyberattacks
However, they’re not perfect. They can’t survey your entire kingdom at once and they might miss things. Ensure you are using a good product – as not all antivirus software is created equal. It serves as your last line of defense, so be sure it is the best at your disposal.
5. Computer & Mobile Device Updates and Security Patches
The fifth cybersecurity tip for your small business are the masons. They work to protect against vulnerabilities. So, make sure to keep your devices, software, and apps updated. This is a critical and easy way to help protect yourself and the company.
In addition to security fixes, software updates can also include new or enhanced features, or better compatibility with different devices or applications. They can also improve the stability of your software and remove outdated features.
6. Have Good Password Hygiene
Passwords are your guards, and they’re often overlooked as a strong aspect of your security. Follow best practices for passwords, have a company password policy, train employees on passwords, consider deploying a companywide password management solution.
7. Regularly Backup Data
Backup your laptops, back up your servers. Backup to your office and replicate it to the cloud. Test your backups. People are not infallible. They make mistakes.
Emails containing viruses are accidentally opened every day and important files are often mistakenly deleted. There’s no reason to fear these issues if you take frequent incremental snapshots of your systems.
8. Use Multi-Factor Authentication
Multi-factor authentication combines two or more independent credentials:
- What the user knows (password)
- What the user has (security token)
- What the user is (biometric verification)
According to Microsoft, MFA alone can block over 99.9 percent of account compromise attacks because it ensures that a weak, lost, or shared password isn’t enough to obtain access to a protected resource. At least one additional authentication factor is necessary, and stealing it is anything but easy.
Utilize Multi-Factor Authentication whenever you can, including:
- On your network
- Banking websites
- Even social media
It adds a layer of protection to ensure that, even if your password does get stolen, your data stays protected.
9. Implement Advanced Cyber Security Monitoring
Advanced cybersecurity monitoring is a dynamic process that goes beyond mere automated alert generation. It requires human judgment, expertise, and an integrated approach to security tools and technologies.
10. Vulnerability Scanning
Test your networks and IT systems on a planned and frequent basis. A vulnerability scan detects and classifies system weaknesses in computers, networks, and communications equipment and can predict the effectiveness of countermeasures.
Bonus Cybersecurity Tip for Small Businesses: Encryption
Encrypt data and communications whenever possible. Data is critical to our personal lives, economic prosperity, and security. That data must be kept secure. Just as we lock our homes, restrict access to critical infrastructure, and protect our valuable business property in the physical world, we rely on encryption to keep cybercriminals from our data.
6 Additional Cybersecurity Tips for Small Businesses
Once you have the 10 foundational elements of cybersecurity in place, then you can start implementing these more advanced measures to further protect your SMB.
Similar to the first ten cybersecurity tips we shared, these risk-mitigating measures are arranged according to the implementation sequence our cybersecurity experts suggest.
11. Get Cyber Insurance
The first more advanced cybersecurity tip for small businesses we recommend is cyber insurance.
Protect your organization by speaking with your attorney and insurance agent about the right sized cyber liability insurance policy for you.
12. Enhance Mobile Device Security
Today’s cybercriminals attempt to steal data or access your network by way of your employees’ phones and tablets. They’re counting on you to neglect this piece of the puzzle. Mobile device security closes this gap.
13. Get SPAM Protection
Secure your company’s email with DMARC, DKIM, and SPF protocols. Most attacks originate in email. And the email solutions we recommend come “baked in” with high-quality SPAM protection.
If your email solution does not, deploy a best-in-class solution designed to reduce spam and your exposure to attacks on your company via email.
14. Have a Managed Firewall
Firewalls are fundamental for protecting a company’s data, computers, and networks. They are required for compliance with mandates like PCI DSS, HIPAA, and GDPR. This is a must-have for all businesses.
Turn on Intrusion Detection and Intrusion Prevention features. Send the log files to a managed SIEM. If your IT team doesn’t know what these things are or you don’t have an IT team, we urge you to look at hiring an MSP to assist you.
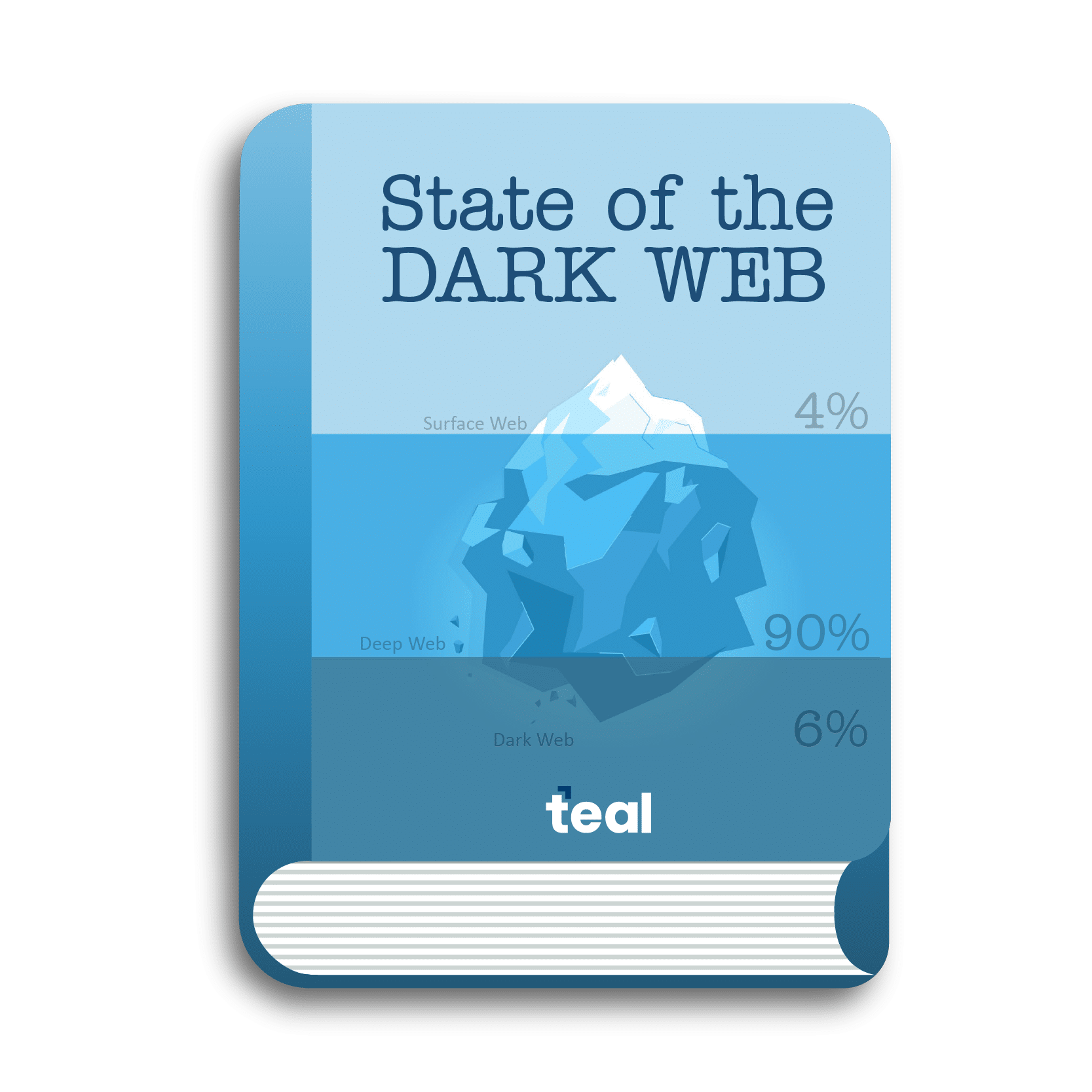
15. Deploy Dark Web Monitoring
Deploy a dark web monitoring solution with search capabilities to identify, analyze, and proactively monitor for an organization’s compromised or stolen employee and customer data.
16. Use Web Security Gateway
Sometimes referred to as a web filter, these solutions detect web and email threats as they emerge on the internet and block them on your network within seconds – before they reach the user.
These gateways may include:
- URL filtering
- Malicious-code detection and filtering
- Application controls for popular web-based applications (e.g., instant messaging)
BONUS: Third Party Risks
Check out what our friends at Vendor Centric have to say about the risks involved when working with third party vendors.
Grow & Secure Your Organization’s Future
Effective cybersecurity is a cornerstone of success for every organization. As a small business leader, embracing robust cybersecurity measures is a proactive step towards safeguarding your company’s future. By prioritizing the right security elements, you are not just preventing potential cyber attacks, but also ensuring the enduring strength and growth of your business.